This explains a research project on how to bypass ARM’s Memory Tagging Extension (MTE), a hardware feature designed to prevent memory corruption vulnerabilities. Here are the key takeaways:
- ARM MTE: MTE works like a “lock and key” system. Pointers have a “key” (a 4-bit tag) and memory objects have a “lock” (also a 4-bit tag). If the key and lock don’t match when a pointer tries to access memory, the program will crash, preventing an attack.
- The Challenge: The tags are randomly generated, making it difficult for an attacker to guess the correct tag to bypass MTE.
- The Attack: The researchers discovered a side-channel attack that combines two CPU features:
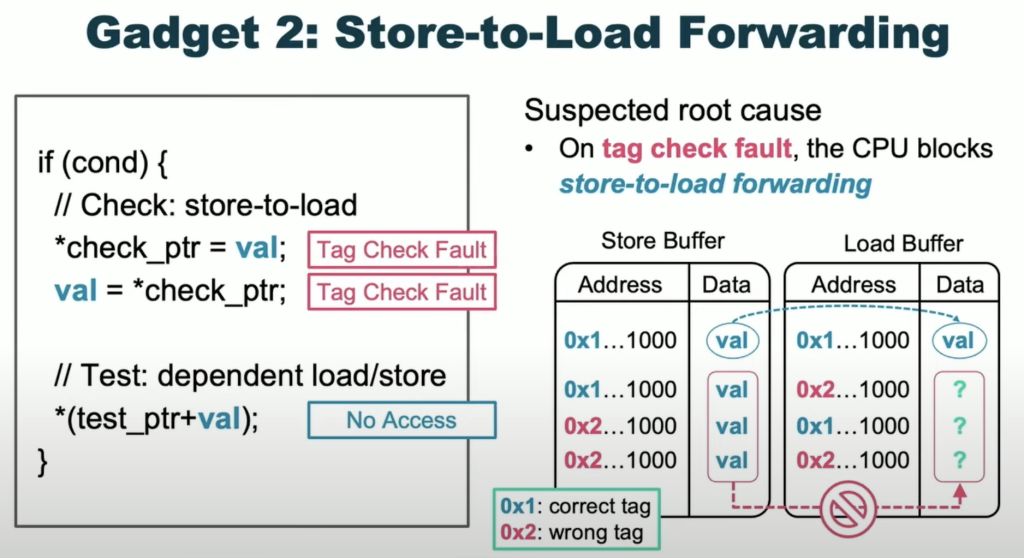
- Cache Side Channel: This allows an attacker to tell if a memory object has been accessed by measuring how long it takes to access it.
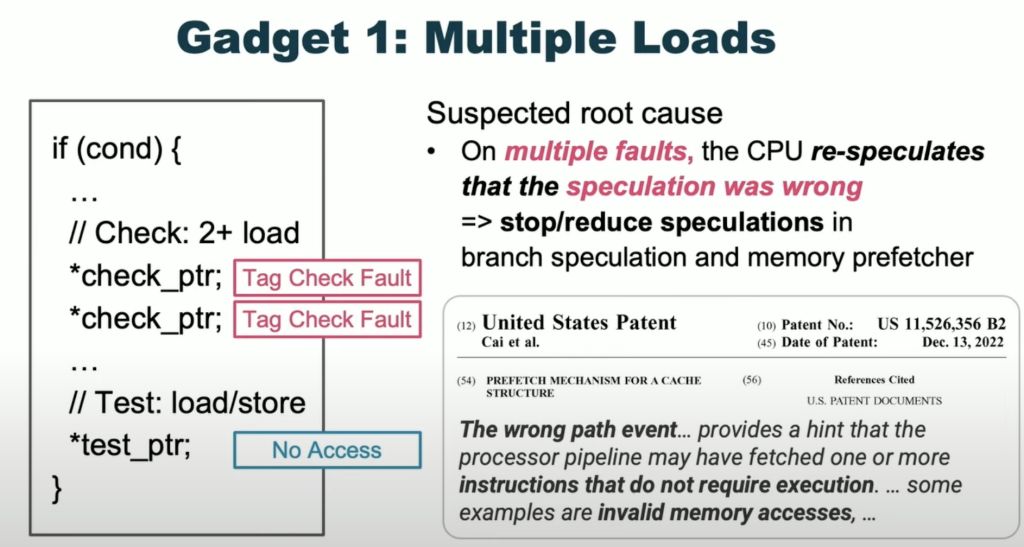
- Speculative Execution: This is a CPU optimization where the processor predicts and executes instructions before they are actually needed. The key finding is that if a tag check fails during speculative execution, the program doesn’t crash immediately.
- Putting it Together: By using these two features, the researchers were able to create “tag leakage gadgets” that leak the MTE tag without crashing the program. This allows them to bypass MTE and exploit memory corruption vulnerabilities.
- Real-World Example: The video demonstrates a real-world attack on Google Chrome’s V8 engine, where they are able to leak the MTE tag of render memory and then exploit a heap overflow vulnerability.
- Vendor Response: While ARM and Google acknowledge the issue, they still consider MTE a valuable security feature. The Chrome V8 team, however, has decided not to adopt MTE in their renderer due to these types of issues.
https://www.computer.org/csdl/proceedings-article/sp/2025/223600a039/21B7QrWwN20