Past
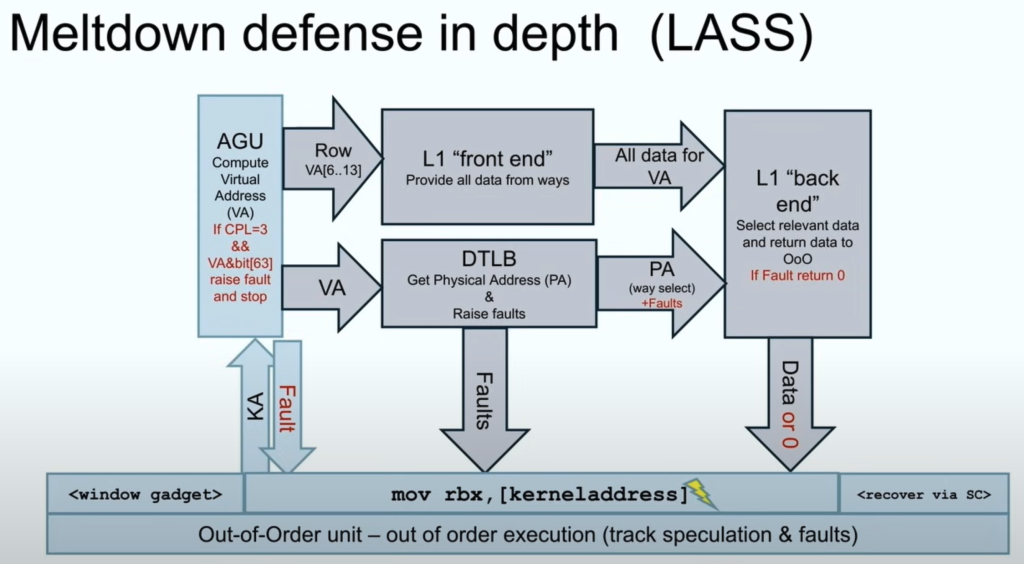
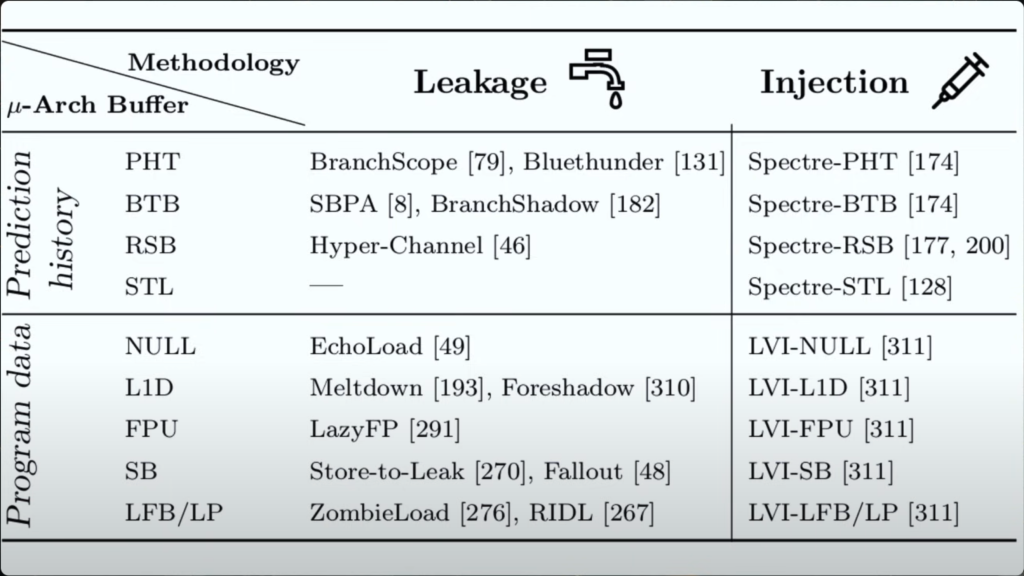
Present
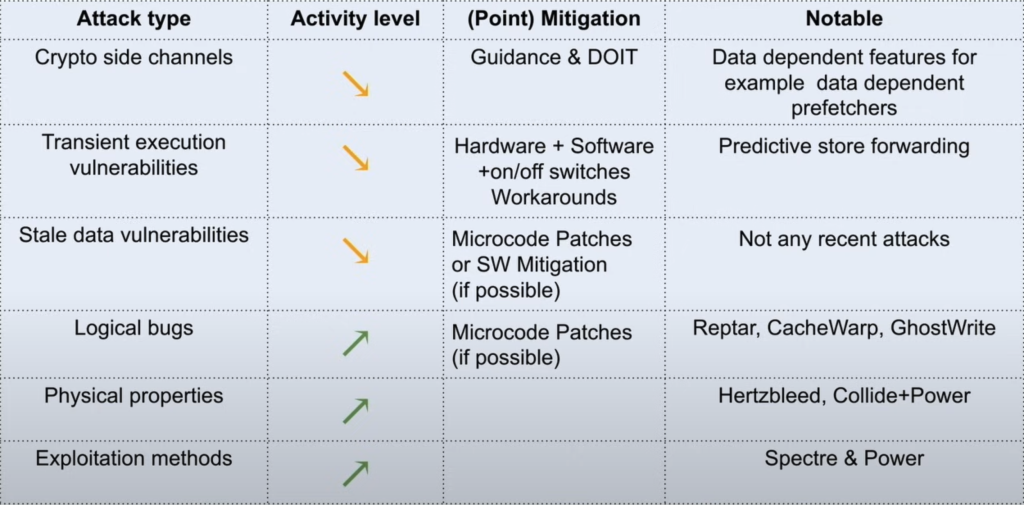
Logic Issues
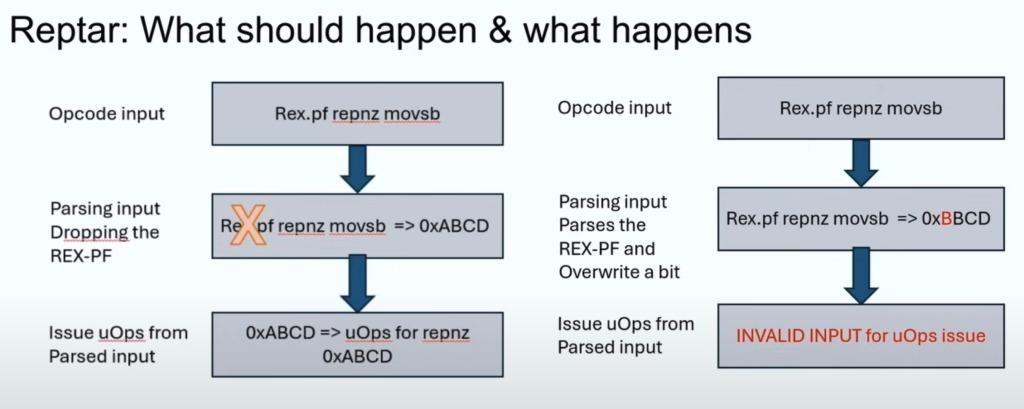
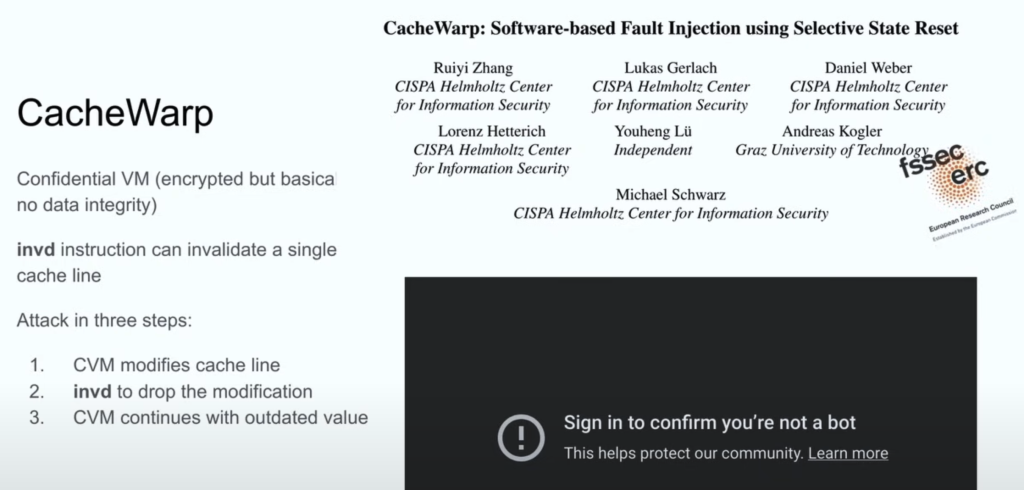
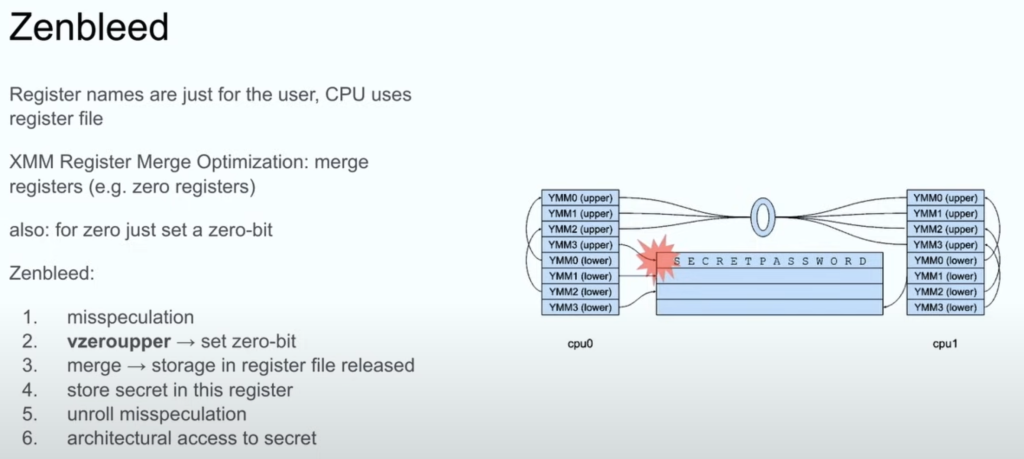
Exploitation Techniques

Physical Domain in Software
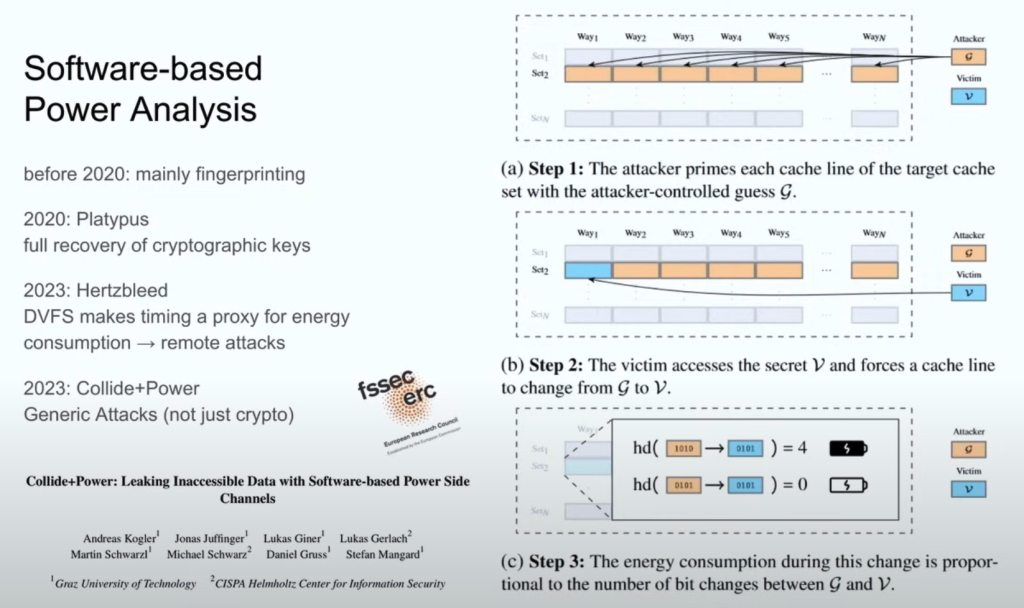
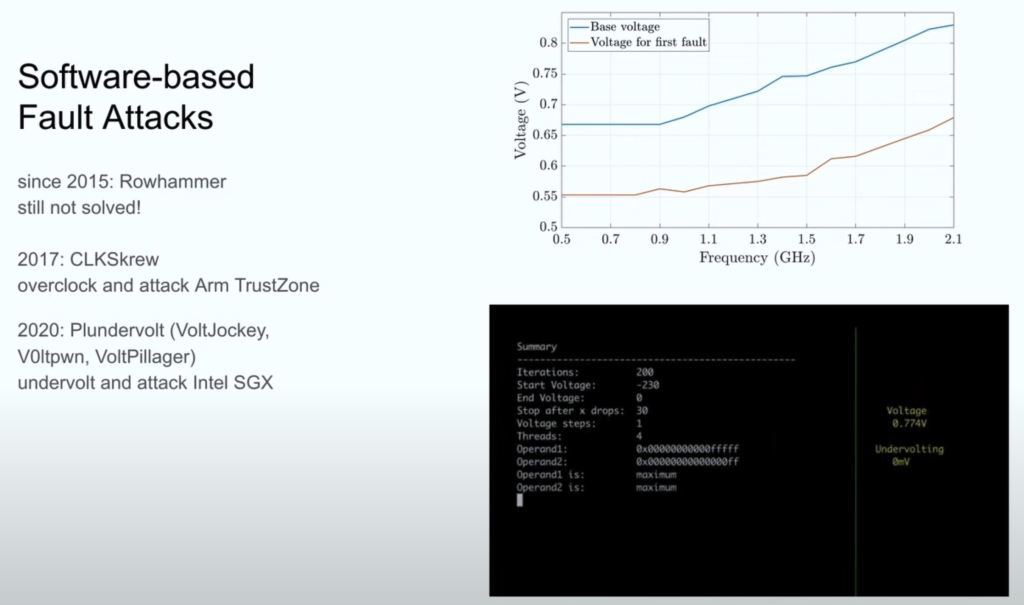
Mitigation Efforts
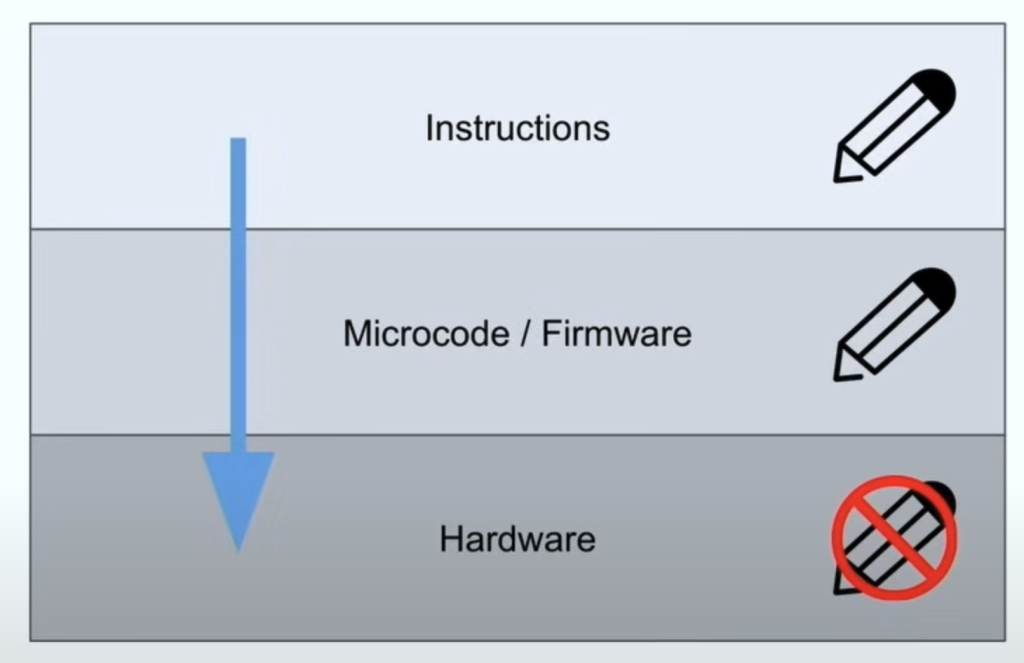
- Physical hardware cannot be changed in the field
- Vendors build in “Survivability features”
- Microcode is the most common used tool for mitigations
- Other firmware is also used
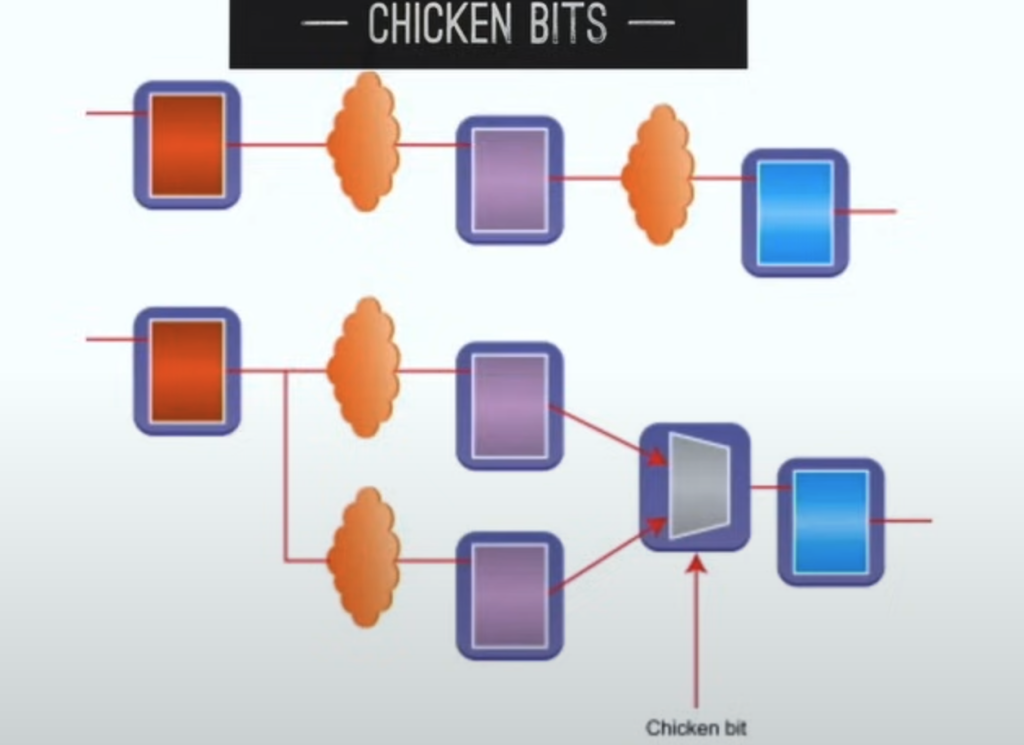
- “Chicken bits” to disable / change behavior
- Some issues are best mitigated in software
- Mitigations are not always possible/reasonable and almost difficult and time-consuming to engineer
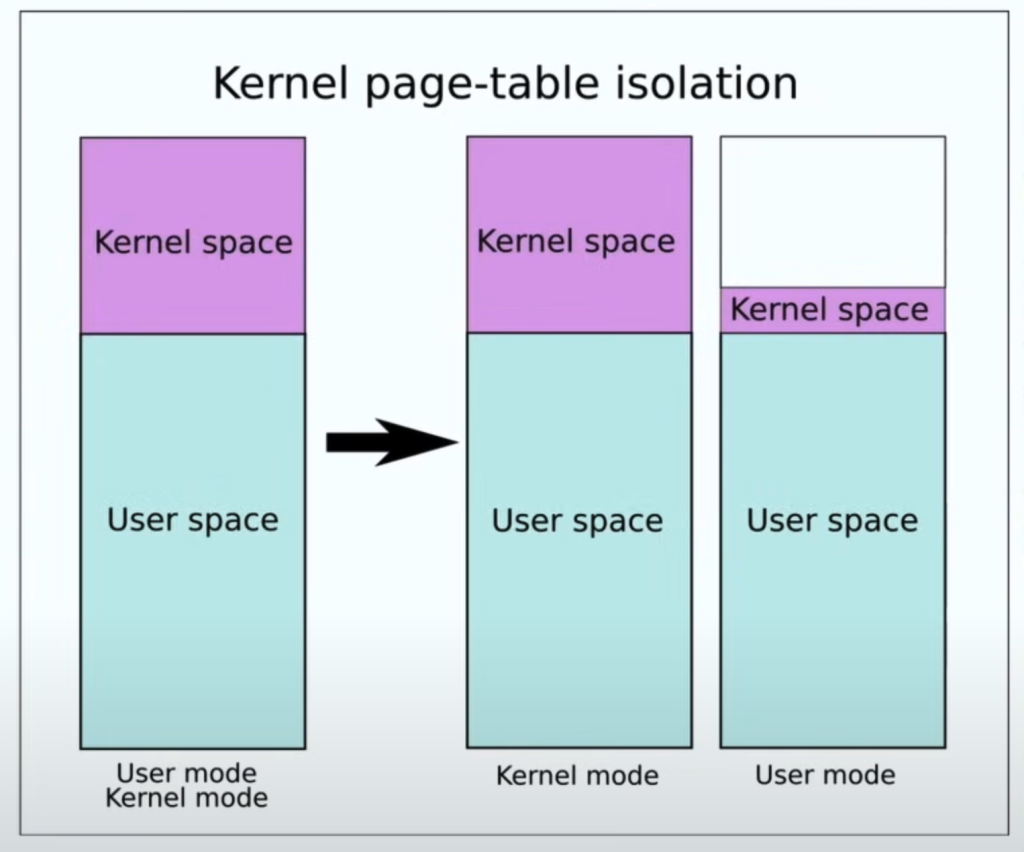
Prevention
Pre-silicon

Post-silicon

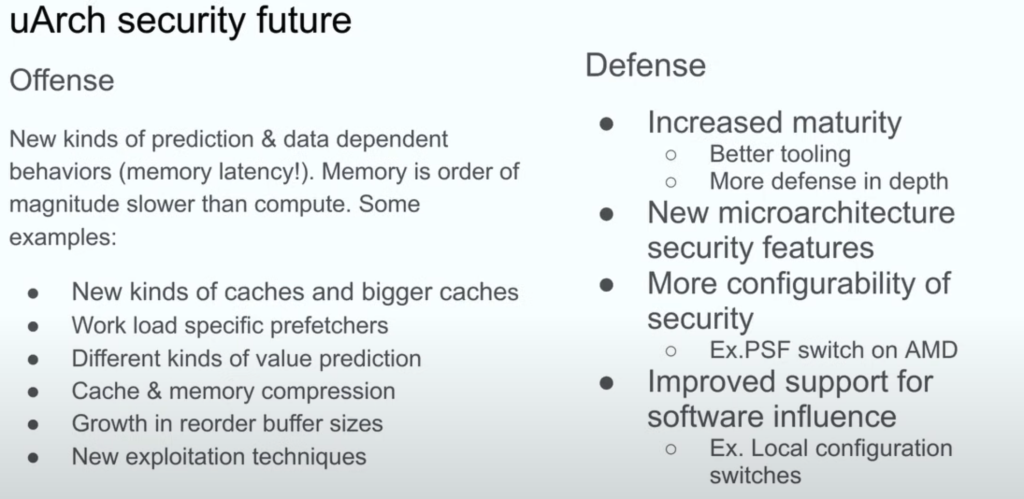
Future


Take Aways
