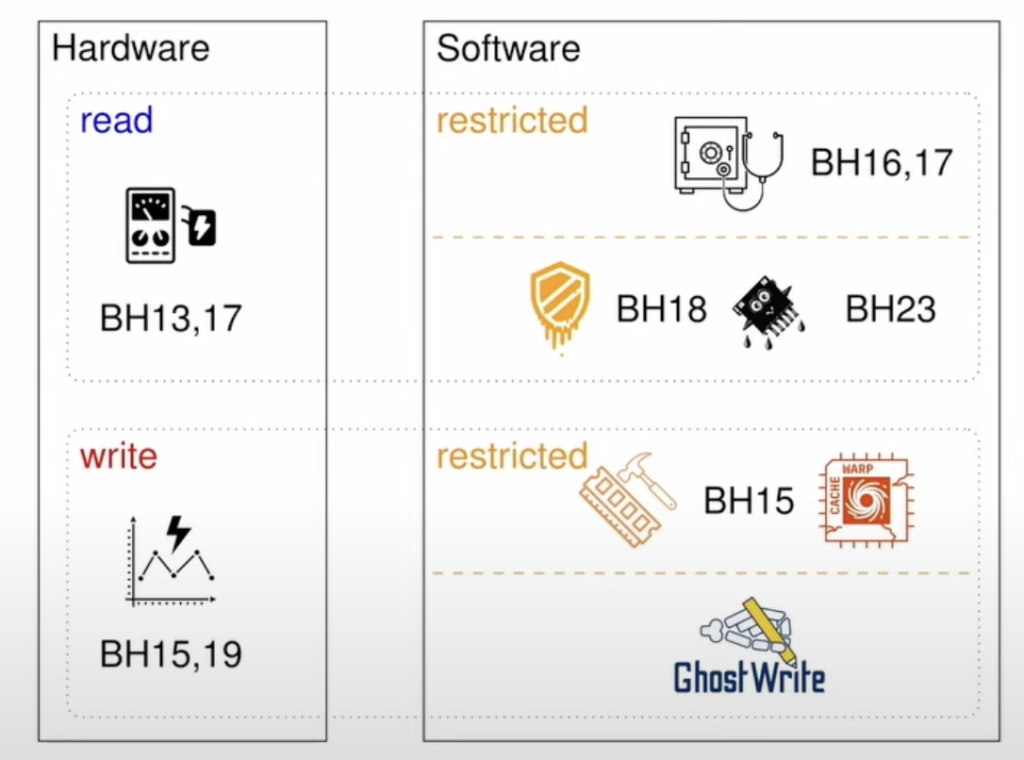
Fabian Thomas and Laurent Schmierer, introduces “GhostRider,” a zero-day vulnerability they discovered in the T-Head C910 RISC-V processor. This vulnerability allows for data manipulation and leakage by bypassing software isolation and writing directly to physical memory.
Here are the key points discussed:
- GhostRider Vulnerability: This exploit allows unprivileged applications to bypass operating systems and other security measures to interact directly with hardware. It exploits a flaw in a RISC-V vector instruction to write to physical memory instead of virtual memory, enabling arbitrary data manipulation, memory leakage, and privilege escalation.
- Affected Hardware: The vulnerability is specific to the T-Head C910 CPU, a high-performance RISC-V processor. The issue is not with the RISC-V standard itself, but with this particular implementation.
- Discovery: The researchers found this vulnerability using a method called “differential fuzzing,” where they compared the behavior of different CPUs running the same programs.
- Mitigation: Since RISC-V cores lack microcode updates, the suggested solution is to disable the Vector Extension through an OS update. This, however, comes with a significant performance reduction.
- Context: The talk places GhostRider in the context of other CPU vulnerabilities, highlighting its unique ability to perform unrestricted and fast memory writes.